Safely Leveraging AI in SEO: Best practices and Google compliance tips
This blog post was distributed through the MarketingSherpa email newsletter.
Although the straightforward use of AI-generated content is not awarded by Google, significant performance benefits can be gained by digital marketers leveraging AI in a responsible and professional manner.
Here are some effective strategies for applying generative AI expertise to escalate one’s performance in SEO and other domains of digital content creation.
I have tried ranking more than 100 template landing pages and blogs with pure AI content, and my experience shows that trying to rank purely AI-based content does not work. The text gets indexed and then deindexed by Google the next day; we did not receive any traffic gains.
But artificial intelligence can assist with content creation. What is received from AI needs to be developed, reviewed and improved to be unique and valuable. Using this approach, I’ve ranked at least 10 blog posts and landing pages for keywords ranked from 20 to 45 competitiveness by the Mangools SERPChecker.
In this article, I’ll show you my process. For this example, I use MeclabsAI (from MarketingSherpa’s parent organization).
But first, let’s review what Google has publicly said about artificial intelligence and content.
Understanding Google’s regulations on AI content
Some marketers believe that generative AI can automatically produce high-quality and SEO-friendly content at scale. Other marketers think AI-generated content will automatically get a Google penalty.
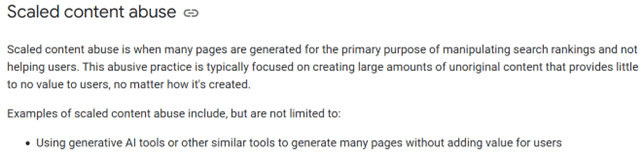
Google’s focus is on the quality of the content and ‘scaled content abuse,’ with its recent March 2024 update. Here is what Google officials say in Spam policies for Google web search:
On the other hand, Google’s attitude towards the manual creation of content that is written using generative AI as an idea contributor is still considered a normal practice to avoid the blank page syndrome, as long as the content is generally aligned with Google’s Helpful Content regulations. Here’s an explanation from the Google Search Central documentation Creating helpful, reliable, people-first content:
Many types of content may have a “How” component to them. That can include automated, AI-generated, and AI-assisted content. Sharing details about the processes involved can help readers and visitors better understand any unique and useful role automation may have served.
If automation is used to substantially generate content, here are some questions to ask yourself:
- Is the use of automation, including AI-generation, self-evident to visitors through disclosures or in other ways?
- Are you providing background about how automation or AI-generation was used to create content?
- Are you explaining why automation or AI was seen as useful to produce content?
Overall, AI or automation disclosures are useful for content where someone might think “How was this created?” Consider adding these when it would be reasonably expected.
Effective strategies for leveraging AI in SEO
Here’s my take on Google’s directions – generative AI tools can provide the main takeaways of the potential article and draft the structure if one starts the writing from scratch. Human writing can expand these ideas further into quality content.
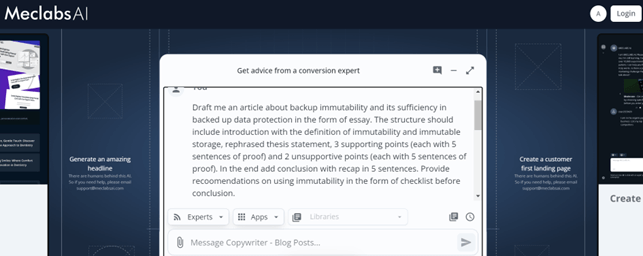
Let me show you what I mean with an example blog post about a topic that would be interesting to potential customers for the backup software company I work at – backup immutability. (If you’re curious, backup immutability refers to the practice of making backup data unchangeable or tamper-proof for a certain period of time).
If I go to Meclabs AI (it is totally free to use, for now) and use this example prompt with the “Copywriter – Blog Posts” expert:
The outcome will be acceptable for a copywriter to start with and then make future enhancements:
Title: The Sufficiency of Backup Immutability in Data Protection: An Analysis
Introduction
In the digital era, where data is ubiquitous and its preservation paramount, the concept of immutability plays a critical role. Immutability, in the context of data storage, refers to the characteristic of data that prevents it from being altered or deleted once it has been written. Immutable storage, therefore, serves as a foundational mechanism for ensuring data integrity and security, providing a safeguard against accidental deletions, malicious alterations, or ransomware attacks. This essay explores the notion that backup immutability sufficiently protects stored data, scrutinizing the strengths and limitations of this approach in maintaining data’s pristine state.
Supporting Points
- Ransomware Resistance
- Ransomware attacks have victimized numerous organizations by encrypting valuable data and demanding ransom for decryption keys. Immutable backups act as a fail-safe, ensuring that even if primary data is compromised, the backup data remains untouched and recoverable. This immutable nature discourages attackers, as they cannot leverage encrypted backups for ransom demands. Statistics show a significant reduction in successful ransomware attacks against entities employing immutable backup strategies. Moreover, immutability complements existing cybersecurity measures by adding an essential layer of defense, enhancing an organization’s resilience against these pervasive threats.
- Regulatory Compliance
- Many industries are governed by stringent regulations mandating the integrity and security of stored data. Implementing immutable storage ensures compliance with such regulations, including HIPAA for healthcare and GDPR for data protection in the EU. Immutable backups provide a verifiable and tamper-evident record of data history, crucial for audits and legal scrutiny. Failure to adhere to these regulations can result in hefty fines and reputational damage, making immutability not just beneficial but necessary for regulatory adherence.
- Data Integrity and Recovery
- Immutable backups preserve the exact state of data at the time of backup, ensuring its integrity. This fidelity is paramount for critical systems where data accuracy and consistency are crucial, such as financial ledgers or legal records. Immutable storage systems employ mechanisms like write-once-read-many (WORM) to guarantee that data remains unaltered once written. In disaster recovery scenarios, this capability ensures that data can be restored to its exact original state, providing businesses with the assurance of continuity.
Unsupportive Points
- Cost and Complexity
- Implementing immutable storage solutions often entails additional costs and complexity. The infrastructure necessary to support immutability can require significant investment in specialized hardware or software solutions. Furthermore, managing these systems introduces complexity into IT operations, necessitating trained personnel and possibly slowing down data retrieval processes. For small to medium-sized enterprises (SMEs), these factors can be prohibitive, leading them to seek less costly, albeit potentially less secure, alternatives.
- Storage Efficiency
- The immutable nature of this storage method can lead to inefficiencies, particularly in terms of storage space. Since data cannot be overwritten or deleted, redundant copies of data can accumulate, consuming valuable storage resources. This not only increases the cost of storage but also complicates data management, making it challenging to navigate vast repositories of immutable data. Technologies such as deduplication and compression can mitigate these effects to some extent, but they cannot fully negate the innate inefficiencies of immutable storage.
Recommendations on Using Immutability
Before concluding, it is beneficial to consider the following recommendations when employing immutability in data protection strategies:
- Assess Needs and Resources: Evaluate your organization’s specific needs and resources to determine if immutability aligns with your data protection goals.
- Regulatory Compliance: Ensure that the chosen immutable storage solution enables compliance with relevant regulatory requirements.
- Infrastructure Evaluation: Assess existing infrastructure to identify potential challenges or required upgrades for supporting immutable storage.
- Cost-Benefit Analysis: Conduct a thorough cost-benefit analysis, considering both the long-term savings from enhanced data protection and the upfront investment.
- Implement in Layers: Integrate immutability as part of a layered security strategy, complementing other cybersecurity and data protection measures.
Conclusion
Backup immutability offers a compelling avenue for ensuring data protection, particularly in its ability to mitigate ransomware attacks, ensure regulatory compliance, and uphold data integrity. However, the considerations of cost, complexity, and storage efficiency present tangible challenges that organizations must navigate. Despite these hurdles, the strategic application of immutable storage, underpinned by a comprehensive analysis and thoughtful planning, can significantly enhance an organization’s data protection capabilities. As we shift towards increasingly digital modes of operation, the role of immutability in safeguarding our digital assets becomes not just relevant but essential, embedding resilience into the fabric of our information systems.
Using AI to help get subject matter experts to contribute to the article’s quality and depth
Beware of posting this directly to your website or blog without reviewing it for accuracy and adding helpful, valuable, and unique insight, as this will trigger non-compliance with the below Google guidelines (from the previously mentioned Google Search Central Documentation):
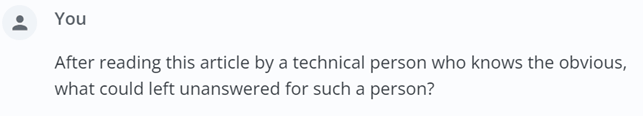
In this particular case, to finalize the article, I usually reach out to the technical team with specific questions about technical details or real-life case studies of immutable systems implementation to obtain the above-mentioned original information. Here is the prompt that I put into MeclabsAI to help me ask the right questions to my technical team:
The output is usually sound. For example, here is the output from MeclabsAI using the “Copywriter – Blog Posts” expert:
After presenting a balanced view on the sufficiency of backup immutability in data protection, several advanced or nuanced questions might still remain unanswered for a technically astute audience. These questions could extend into areas requiring deeper exploration or touch on emerging problems in the field. Some potential questions left unanswered for a technical professional might include:
- Performance Impact: How does immutability affect the performance of backup and recovery processes, particularly in environments with large datasets or high transaction volumes? The essay does not delve into the specifics of performance degradation or optimization techniques.
- Scalability Concerns: Can immutable storage solutions scale efficiently to meet the demands of exponentially growing data, and what are the best practices for ensuring scalability without compromising on the system’s inherent security and integrity features?
- Legal and Ethical Implications: There might be legal or ethical questions around immutability, especially regarding the right to be forgotten under GDPR and how it reconciles with immutable records. The complexities of managing immutable storage in a legally compliant manner remain unaddressed.
- Advanced Threat Vectors: While ransomware is mentioned, the discussion on evolving cybersecurity threats that might circumvent or exploit immutable backups is missing. For instance, how might sophisticated attacks leverage or impact immutable storage differently?
- Immutable Storage Technologies: The article does not explore the specific technologies that enable immutability, such as blockchain for data storage or advanced WORM drives. A technical person might seek detailed comparisons or evaluations of different technologies supporting immutability.
- Integration with Existing Systems: The practicalities of integrating immutable storage solutions into an existing data management and protection ecosystem are not discussed. How do organizations navigate the transition, and what are the potential interoperability challenges?
- Cost Management Strategies: While the costs are mentioned as a drawback, the essay does not offer strategies for managing or offsetting these costs, especially over the long term. Are there emerging cost-effective solutions or innovative funding models that can support the deployment of immutable storage?
- Data Lifecycle Management: How does immutability impact data lifecycle management policies? The process of managing data from creation to deletion, especially in the context of immutable storage, is not addressed, including data retention policies and compliance implications.
- Technical Evolution and Future Prospects: What are the future developments anticipated in the realm of immutable storage? This could include advancements in technology, regulatory changes, or evolving best practices in data protection.
Addressing these questions would provide a deeper, more nuanced understanding of backup immutability’s role in data protection, catering to a technical audience familiar with the basics.
Based on this output, I will get technical feedback and write the content that benefits the readership and provides unique value compared to other search results, which is the key to a successful ranking. It is also much easier for my colleagues from technical departments to contribute because, instead of asking for any possible input, I request specific things to be added. Indeed, as a digital marketer, I don’t have enough knowledge to contribute the ideas myself, and in this scenario AI provides significant productivity gains for both my colleagues and me.
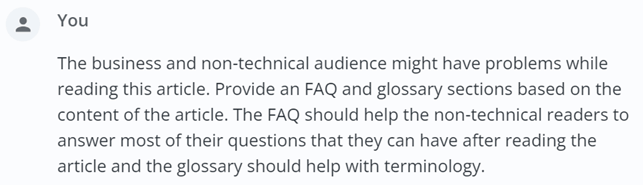
AI prompt for creating helpful background and summary content from your original content
Here is another prompt that I find useful to make the content even more helpful, especially for various audiences:
The FAQ and Glossary sections are designed to assist non-technical readers in understanding the key concepts and benefits associated with backup immutability, providing a clearer insight into how it fits into broader data protection strategies. Here is the output I got from MeclabsAI using the “Copywriter – Blog Posts” expert:
FAQ Section
What is backup immutability?
Backup immutability is a feature of some storage systems that prevents data from being altered or deleted once it’s been saved. This means once you back up your data, it cannot be changed, ensuring its original state is preserved even in the event of a cyber-attack or accidental deletion.
Why is ransomware resistance important?
Ransomware resistance is crucial because it means that even if a hacker locks up your data, demanding payment to unlock it, you can restore your information from immutable backups without paying the ransom. It helps keep your data safe and your business running without giving in to cybercriminal demands.
How does immutable storage help with regulatory compliance?
Immutable storage helps meet strict rules set by governing bodies for data storage by ensuring that sensitive information cannot be tampered with. This is important for industries like healthcare and finance, where data integrity is critical.
What are the potential downsides of immutable storage?
The primary downsides include the increased cost and complexity of managing immutable storage systems and inefficiencies related to storage space usage, as data cannot be overwritten or easily deleted.
Can small businesses afford immutable storage?
While immutable storage can be more expensive, it’s about weighing the costs against the potential losses from a data breach or ransomware attack. Small businesses should consider the value of their data and regulatory requirements when deciding.
What should I consider before implementing immutability?
Before going ahead, consider your business needs, regulatory compliance requirements, existing infrastructure, and the cost versus benefits of using immutable storage. Also, think about how it will fit into your broader data protection strategy.
Glossary Section
- Backup Immutability: The property that ensures backup data cannot be changed or deleted after being stored.
- Immutable Storage: Storage systems designed to make data unchangeable and undeletable once written.
- Ransomware: Malicious software that encrypts a victim’s files, with the attacker then demanding payment for their decryption.
- HIPAA: The Health Insurance Portability and Accountability Act, U.S. legislation that provides data privacy and security provisions for safeguarding medical information.
- GDPR: General Data Protection Regulation, a regulation in EU law on data protection and privacy in the European Union and the European Economic Area.
- Data Integrity: The accuracy, completeness, and reliability of data throughout its lifecycle.
- WORM (Write Once, Read Many): A data storage technology that allows data to be written to a device a single time and prevents the data from being erased or modified.
- Regulatory Compliance: Adhering to laws, regulations, guidelines, and specifications relevant to business operations.
This FAQ and glossary are designed to help non-technical readers understand key concepts and considerations mentioned in the article, offering a clearer insight into the importance and intricacies of backup immutability in data protection.
Other ways AI can enhance productivity and quality for SEO and content marketing
In addition, I consider automating the creation of metadata such as descriptions, URL slugs, titles, and headings to be an effective method of leveraging AI for productivity. When I put this prompt into MeclabsAI using the “Copywriter – Blog Posts” expert:
I get this output from MeclabsAI:
Metadata Proposal for the Article
Meta Title: Immutable Backup Solutions: Ensuring Data Protection Against Ransomware
Meta Description: Explore the critical role of backup immutability in safeguarding data. Discover how immutable backup solutions can provide a robust defense against ransomware attacks, ensuring regulatory compliance and data integrity.
URL Slug: immutable-backup-solutions-data-protection
H1: Immutable Backup: The Key to Reliable Data Protection Against Ransomware
This metadata is crafted to highlight the core themes of the article while incorporating the targeted keywords to optimize search engine visibility. It emphasizes the importance of immutable backup solutions in protecting against ransomware, catering to readers seeking robust data protection strategies.
These metadata elements are designed for those who specifically search for immutable backup solutions and their effectiveness in combating ransomware.
Before posting I recommend you use the following prompt to ensure you have a high-quality article. For my example, I added some notable websites from “immutable backup” search results:
After I put this prompt into MeclabsAI using the “Copywriter – Blog Posts” expert, I got this response:
Given the limitations of accessing the full content directly from the URLs due to the structure or access restrictions of the websites, making a direct and comprehensive comparison between the proposed article and those on Rubrik and Veeam’s websites is challenging. However, based on the information available, here are some considerations and hypothetical reasons why one article might be better than another, focusing on general strengths and potential content coverage based on accessible summaries and insight into the topics discussed:
Proposed Article Strengths:
- Balanced Analysis: The proposed article promises a balanced discussion by exploring both the advantages and limitations of immutable backups, which could provide readers with a nuanced understanding of the topic.
- Educational Value: Including an FAQ and glossary section caters to both beginners and more advanced readers, ensuring the content is accessible to a broad audience.
- Structured Argumentation: The article’s structure, with supporting and unsupportive points, allows for a well-organized argument that’s easy to follow.
Rubrik’s Immutable Data Backup Webpage:
- Brand Authority: Rubrik, specializing in data protection and cybersecurity, offers content that likely draws on deep industry expertise and practical experience.
- Product Integration: Their discussion of immutable data backup may include specific product examples and integration scenarios, offering tangible application cases to readers.
- Industry Insights: Given Rubrik’s positioning in the market, their content might include unique insights into industry trends and future directions of immutable backup solutions.
Veeam’s Immutable Backup Webpage:
- Technical Detail: Veeam is known for providing technically rich content, which may offer readers a deeper dive into the workings and specifics of immutable backup technology.
- Solution-Oriented: Their content probably emphasizes practical solutions, showcasing how their products address the challenge of data immutability and protection against ransomware.
- Broad Application: Given Veeam’s wide-ranging product suite, their article might cover a variety of use cases and environments where immutable backups can be effectively deployed.
Comparative Analysis:
- Content Depth: If Veeam’s and Rubrik’s articles delve deeply into technical specifics and practical applications, they might offer more for readers seeking in-depth, actionable insights compared to a general overview.
- Audience Engagement: The proposed article, with its structured argumentation and inclusion of an FAQ and glossary, may be more engaging for non-technical readers or those new to the concept of immutable backups.
- Practical Application vs. Conceptual Understanding: Articles from Veeam and Rubrik likely focus on practical applications within their product ecosystems, which is invaluable for users of their platforms. In contrast, the proposed article aims for a conceptual understanding, potentially offering a broader perspective on the issue.
Ultimately, the “better” article depends on Google’s objectives: seeking foundational understanding, a balanced viewpoint, and requiring deep technical insights tied to specific products. To better understand next writing steps, I add the following prompt into MeclabsAI using the “Copywriter – Blog Posts” expert:
MeclabsAI gave me the following output:
To elevate the proposed text beyond what is offered by Veeam’s content, particularly focusing on the advantages Veeam typically brings to its articles, consider the following enhancements which couple the strengths of both in-depth technical insights and broad, engaging content:
Technical Demonstrations and Use Cases
- In-Depth Technical Illustrations: Provide detailed diagrams or schematics that break down how immutable backup operates at a technical level. These could include flowcharts of the backup process, data lifecycle stages, or architecture diagrams showing the integration of immutable backup in various IT environments.
- Real-World Use Cases: Include case studies or examples from real businesses that have successfully implemented immutable backup solutions. Discussing specific scenarios where immutable backup prevented data loss due to ransomware attacks would be particularly compelling.
Integration and Implementation Focus
- Step-by-Step Implementation Guides: Offer a comprehensive guide on implementing immutable backups within existing IT infrastructures, addressing common challenges and providing solutions.
- Integration with Broader IT Ecosystems: Discuss how immutable backups can integrate with other IT security measures, such as endpoint protection, network security, and disaster recovery planning, to create a holistic data protection strategy.
Forward-Looking Insights
- Future Trends in Data Protection: Analyze emerging technologies and methodologies in data protection, such as AI-driven threat detection and blockchain for data integrity, and speculate on how these could enhance or interact with immutable backups in the future.
- Expert Commentary: Include interviews or quotes from industry experts discussing the evolution of immutable backups and their view on future challenges and opportunities in data protection.
Enhanced Reader Engagement
- Interactive Content: Integrate interactive elements such as quizzes to help readers assess their need for immutable backups or calculators to estimate cost savings from avoiding ransomware attacks.
- Community and Support Insights: Create a section dedicated to community questions, insights, and support where readers can share their experiences, challenges, and solutions related to implementing immutable backup solutions.
Comprehensive Security Perspective
- Broader Cybersecurity Framework Inclusion: Situate immutable backups within a comprehensive cybersecurity framework, discussing their role alongside other cybersecurity practices in mitigating risks across different vectors.
Technical Comparatives
- Comparison with Other Backup Technologies: Provide a comparative analysis of immutable backups versus traditional backups and other modern data protection approaches, highlighting pros, cons, and best-fit scenarios for each.
By addressing these areas, the improved article would not only rectify the weaknesses identified but also surpass the technical detail and practical utility typical of competitor’s content, offering a more compelling and valuable resource for readers.
Conclusion: AI has a role in content creation, not the only role
Overall, while SEO managers still need a deep dive into the topic they are writing about to understand the potential search intent and generate helpful and valuable content, AI can help with the structure, contents, thesis, and supporting points, thereby enhancing productivity. Here are some tips to use AI responsibly:
- Use AI only for preliminary research and idea generation but always verify the factual correctness of the output
- Enhance content quality with AI-driven insights only if the content undergoes significant human editing and enhancement
- Leverage AI for quality control and competitive comparison
- Always openly disclose AI usage and use it with ethical considerations in all sectors
- Use AI in compliance with data protection laws and other regulations
For SEO experts, becoming proficient in safe generative AI use provides a crucial advantage in a field where keeping pace with technology is essential. As AI reshapes the SEO industry, those who develop these skills not only solidify their client success but also unlock new possibilities within the future.
Legal disclaimer
The information provided in this article is for general informational purposes only. All information in the article is provided in good faith, however, we make no representation or warranty of any kind, express or implied, regarding the accuracy, adequacy, validity, reliability, availability, or completeness of any information in the article.
Under no circumstance shall we have any liability for any loss or damage of any kind incurred as a result of the use of the site or reliance on any information provided in the article. Your use of the article and your reliance on any information in the article is solely at your own risk.
Please consult with a professional before making any decisions based on the information provided. The use of AI and compliance with Google’s guidelines should be approached with caution and professional guidance to ensure best practices are followed.
About the author
Andrei Iunisov is an independent digital marketing and SEO expert with 15 years of worldwide experience. Since 2006 Andrei has been involved in digital marketing for the rapidly growing software company Parallels in the USA. In 2009 he co-founded one of the first Google-certified web analytics agencies in CIS. In 2014 the business was sold to the largest independent digital marketing group in Russia – iConText Group. Since 2016 Andrei has provided individual digital marketing services to various technology companies worldwide. You can follow him on LinkedIn.
Related resources
What Is Marketing Optimization: Examples of SEO, CRO, and website speed optimization
Categories: Search Marketing artificial intelligence, Commonwealth of Independent States, European Union, frequently askes questions, General Data Protection Regulation, heading, Health Insurance Portability and Accountability Act, search engine optimization, search engine results page, uniform resource locator, United States, United States of America, write once read many